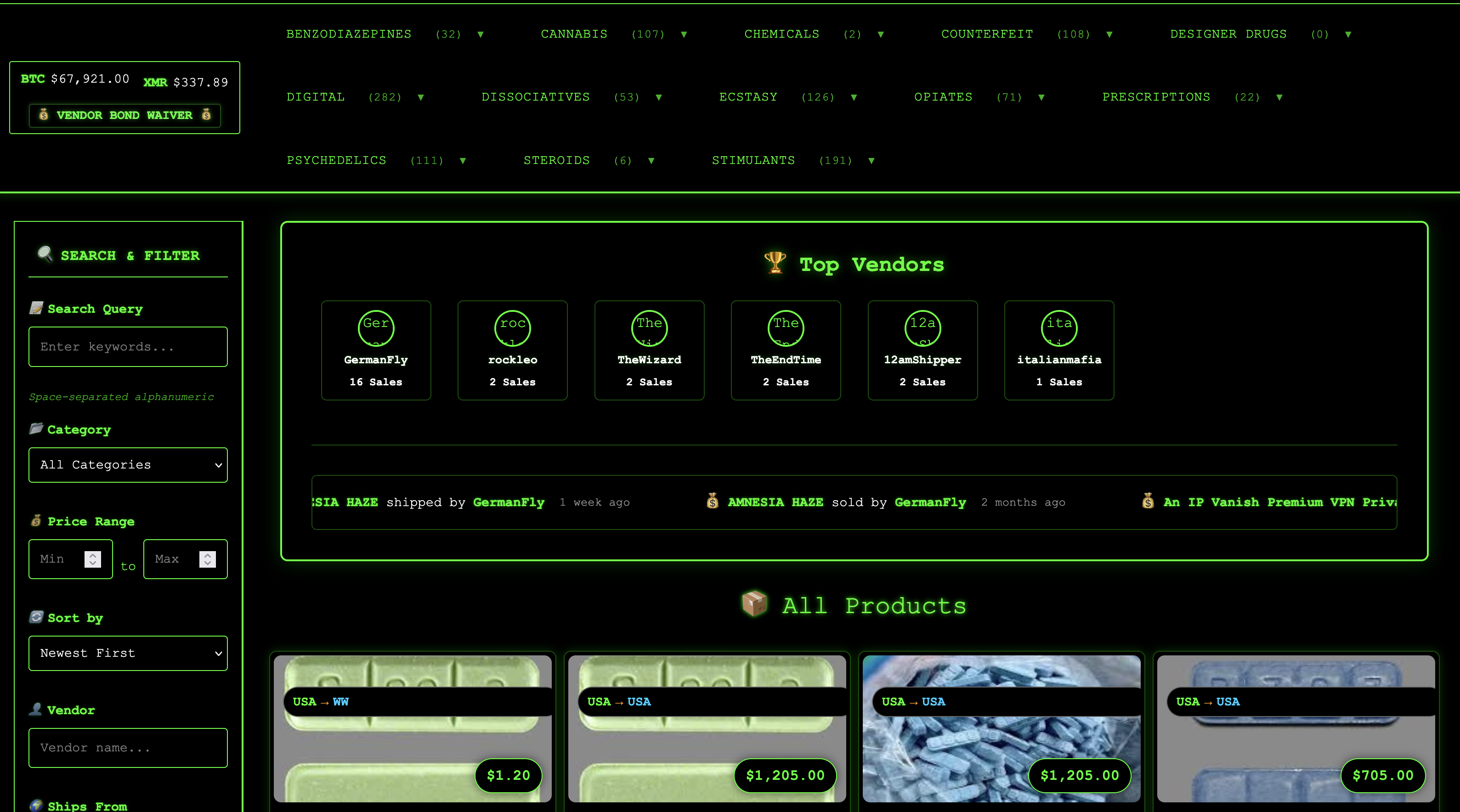
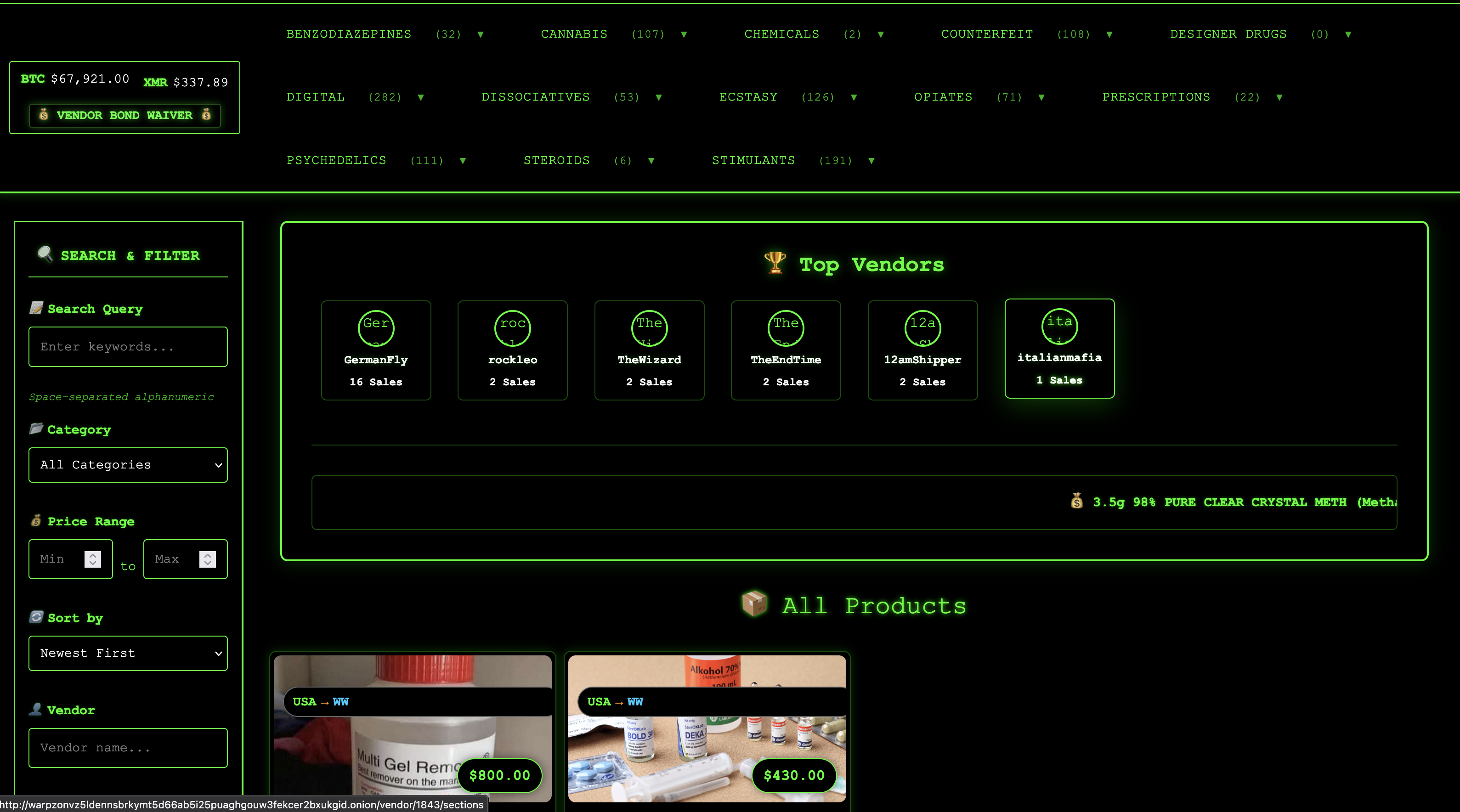
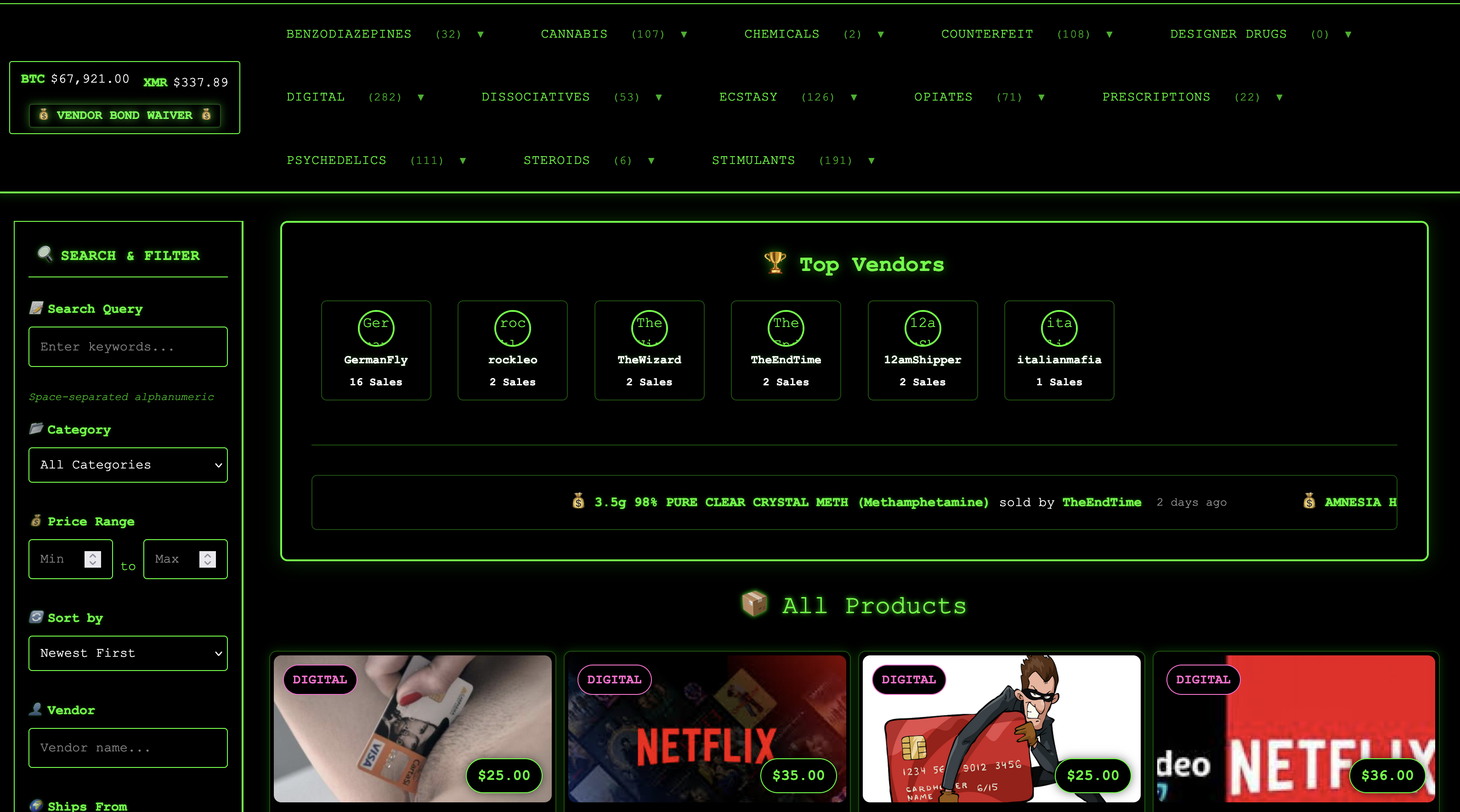
Warpzon Market Preview
Warpzon Market — Official Links, Verified URLs, and Safe Access
The internet as most people know it represents only a fraction of what actually exists online. Beneath the surface web — the part indexed by Google, Bing, and other mainstream search engines — lies a vast, largely unmapped territory known as the deep web. Within the deep web exists the darknet, a collection of overlay networks that require specific software, configurations, or authorization to access. The darknet is not a single place but rather a constellation of hidden services and encrypted channels designed to preserve user anonymity and resist censorship.
Warpzon Market serves as an informational resource dedicated to exploring the technologies, tools, and philosophies that underpin this hidden layer of the internet. Our goal is not to glorify or condemn the darknet but to provide clear, accurate, and actionable information for those who seek to understand how online anonymity works, why it matters, and how individuals can protect their digital footprint in an era of unprecedented surveillance.
Whether you are a journalist investigating corruption in an authoritarian regime, a privacy advocate pushing back against corporate data harvesting, a security researcher studying threat landscapes, or simply a curious individual who believes in the fundamental right to communicate without being watched, this portal offers the knowledge you need to navigate these technologies safely and responsibly.
What Is the Darknet and How Does It Differ from the Deep Web
The terms "deep web" and "darknet" are often used interchangeably in mainstream media, but they refer to fundamentally different things. The deep web encompasses all web content not indexed by standard search engines. This includes private databases, academic repositories behind paywalls, corporate intranets, medical records, legal documents, and any page that requires authentication to view. By some estimates, the deep web is hundreds of times larger than the surface web.
The darknet, by contrast, is a deliberate construction. It consists of networks overlaid on top of the regular internet infrastructure that use non-standard protocols and encryption to anonymize both the users and the hosts of websites and services. The most widely known darknet is the Tor network, but others include I2P (the Invisible Internet Project), Freenet, and Zeronet. Each has different architectures, trade-offs, and use cases, but all share a common goal: enabling communication and information sharing that cannot be easily monitored, censored, or traced back to any individual.
Accessing the darknet typically requires specialized software. For the Tor network, this means using the Tor Browser, a modified version of Mozilla Firefox preconfigured to route all traffic through the Tor relay network. For I2P, users install a router daemon that creates encrypted tunnels for all network traffic. These tools are not illegal in most jurisdictions — they are open-source software available for anyone to download and use. What makes them powerful, and sometimes controversial, is the degree of anonymity they provide.
It is critical to understand that the darknet itself is neither inherently good nor evil. Like any technology, its nature depends entirely on how it is used. The same network that allows a dissident to communicate securely can also be exploited by malicious actors. This duality is what makes the darknet one of the most fascinating and important areas of modern internet infrastructure to study and understand.
The Tor Network — How Onion Routing Preserves Anonymity
The Tor network remains the most popular and well-studied anonymity network in existence. Originally developed by the United States Naval Research Laboratory in the mid-1990s, Tor was designed to protect government communications. The project was later released as open-source software and is now maintained by the Tor Project, a nonprofit organization dedicated to advancing human rights and freedoms by creating and deploying free and open anonymity and privacy technologies.
At its core, Tor works through a process called onion routing. When a user sends a request through the Tor network, that request is encrypted in multiple layers — like the layers of an onion. The request then passes through a series of volunteer-operated relays, typically three: an entry node (guard), a middle relay, and an exit node. Each relay peels off one layer of encryption, revealing only the address of the next relay in the chain. No single relay knows both the origin and the destination of the traffic.
The entry node knows who you are (your IP address) but not what you are requesting. The middle relay knows nothing about either end. The exit node knows what is being requested but not who is requesting it. This separation of knowledge is what makes Tor effective at preserving anonymity. Even if one relay is compromised, the attacker cannot correlate the traffic without controlling all three relays simultaneously — a scenario that becomes increasingly unlikely as the network grows.
Beyond simply anonymizing web browsing, Tor supports hidden services (now called onion services) — websites hosted within the Tor network itself. These sites use .onion addresses and their physical server locations are concealed from both users and outside observers. Onion services provide mutual anonymity: neither the user nor the server knows the other's IP address. This architecture has proven invaluable for whistleblowing platforms, secure communications, and privacy-critical applications.
A Brief History of Darknet Technologies
The concept of anonymous digital communication predates the modern internet. In the 1980s, David Chaum published groundbreaking papers on anonymous communication networks and digital cash systems. His work laid the theoretical foundation for technologies that would emerge decades later. The cypherpunk movement of the early 1990s — a loosely organized group of cryptographers, programmers, and privacy advocates — took these ideas further, developing practical tools like PGP (Pretty Good Privacy) encryption, anonymous remailers, and early proposals for digital currencies.
The first modern darknet emerged with Freenet in 2000, created by Ian Clarke as a peer-to-peer platform for censorship-resistant communication. Freenet allowed users to share files and publish websites anonymously using a distributed data store. While groundbreaking, Freenet suffered from performance issues and a steep learning curve that limited its adoption.
Tor followed in 2002, with the alpha version released by Roger Dingledine and Nick Mathewson. The Tor Browser Bundle, which made using the network accessible to non-technical users, was first released in 2008. This was a watershed moment — suddenly, anyone with a standard computer could browse the internet anonymously without needing to understand the underlying cryptography.
I2P launched around the same time as Tor but took a fundamentally different architectural approach. Rather than providing anonymous access to the regular internet, I2P focused on creating an internal network of services — a network within a network. This design decision made I2P particularly resilient against certain attacks but also meant its user base remained smaller and more specialized.
The 2010s saw an explosion of darknet activity and public awareness. The Silk Road marketplace, launched in 2011, brought the concept of darknet markets into mainstream consciousness. Its closure by the FBI in 2013 — and the arrest of its alleged founder Ross Ulbricht — became one of the most significant law enforcement operations in internet history and sparked ongoing debates about privacy, freedom, and the limits of government authority in digital spaces.
Why Digital Privacy Matters More Than Ever
In 2013, Edward Snowden's revelations about the scope of mass surveillance programs operated by the NSA and its Five Eyes partners fundamentally changed the public conversation about digital privacy. Documents leaked by Snowden showed that intelligence agencies were collecting metadata on virtually all phone calls made in the United States, intercepting internet communications at major backbone junctions, and working to undermine encryption standards. These disclosures confirmed what privacy advocates had long suspected: that the infrastructure of the internet had been co-opted for mass surveillance on an unprecedented scale.
Since then, the situation has only intensified. Governments around the world have expanded their surveillance capabilities, often under the banner of national security or combating terrorism. Companies like Google, Facebook (now Meta), and Amazon collect vast quantities of personal data to fuel their advertising businesses. Data breaches expose millions of records annually. In this environment, tools that protect anonymity and encrypt communications are not luxuries — they are necessities for anyone who takes their privacy seriously.
The importance of these tools extends far beyond individual privacy. Journalists use Tor and encrypted messaging to communicate with sources in countries where press freedom does not exist. Human rights organizations use darknet technologies to document abuses in conflict zones. Whistleblowers use anonymous channels to expose corporate fraud, government corruption, and environmental crimes. Without these tools, many of the most important revelations of the past two decades would never have come to light.
Getting Started — Your First Steps Toward Anonymity
For those new to the world of digital anonymity, the volume of information can be overwhelming. The good news is that getting started does not require a computer science degree or specialized hardware. The most important first step is understanding your threat model — who or what are you trying to protect yourself from, and what are the consequences if your anonymity is compromised? A casual user seeking to avoid targeted advertising has very different needs from a journalist protecting a source in a hostile country.
For basic privacy protection, start with the Tor Browser. Download it exclusively from the official Tor Project website at torproject.org. The Tor Browser is available for Windows, macOS, Linux, and Android. It comes preconfigured for security and requires no additional setup. Simply install it and start browsing. Be aware that Tor will be slower than your regular browser because your traffic is being routed through multiple relays around the world — this is the trade-off for anonymity.
Beyond the browser, consider adopting encrypted messaging applications like Signal for everyday communications. Use a reputable VPN service as an additional layer of protection, though understand that a VPN alone does not provide the same level of anonymity as Tor. Familiarize yourself with PGP encryption for securing emails and files. And if your threat model demands it, explore privacy-focused operating systems like Tails (which routes all traffic through Tor and leaves no trace on the host machine) or Whonix (which runs Tor in an isolated virtual machine environment).
Essential Reading and Resources
Articles on This Site
- VPN vs Tor — Which One Should You Use and When
- PGP Encryption Basics — Securing Your Communications
- Getting Started with Tails OS — The Amnesic System
- Operational Security Fundamentals for Darknet Users
- Bitcoin Privacy — Understanding Blockchain Analysis and Countermeasures
External Resources
- EFF Surveillance Self-Defense Guide — comprehensive guide to protecting yourself from electronic surveillance
- Privacy Guides — independent, community-driven resource for privacy tools and knowledge
- Whonix Documentation — detailed technical documentation on running anonymous systems
- Tor Project — History — the official history of the Tor network
- EFF Privacy Issues — ongoing coverage of digital privacy battles
GitHub Repositories
- github.com/torproject — official Tor Project source code and tools
- github.com/Lissy93/awesome-privacy — curated list of privacy and security-focused software
- github.com/ajvb/awesome-tor — curated list of Tor-related projects and resources
Communities and Forums
- r/privacy — Reddit community with 1.5M+ members discussing digital privacy
- r/TOR — Reddit community focused on the Tor network
- Privacy Guides Forum — community forum for privacy tool discussions